FAQ
What is Payment Fraud?

Payment fraud is a prevalent financial crime in today’s global and connected business world. It usually involves a fake or illegal money transfer committed by a criminal. It victimizes many organizations both in terms of financial losses and reputational damage.
Table of Contents
Types of Payment Fraud
Fraud takes many forms. For consumers, some prevailing payment fraud examples are:
- Credit card fraud: fraudsters can steal credit card information through phishing – pretending to represent legitimate businesses and asking for card details, or skimming – installing small devices on payment terminals to record card information.
- Account takeover fraud: this type of fraud occurs when a criminal obtains a victim’s bank account login credentials to steal funds and/or information. Criminals can take over existing bank, credit card and ecommerce accounts, resulting in unauthorized transactions, credit card fraud and suspicious shopping sprees.
- Gift card fraud: gift cards are similar to cash and scammers exploit this by contacting victims with urgent situations, instructing them to purchase gift cards from specific stores, and providing the card numbers and PINs to access the loaded money, resulting in permanent loss of money for the victim.
For corporations, the following types of payment fraud are commonly seen:
- Business email compromise (BEC): BEC scams typically begin with an urgent email sent to an employee that appears to come from a senior level official, requesting a money transfer. A variation of this scam consists of emailed invoices that appear to come from a routine supplier that have new instructions on where to send payment.
- Check fraud and Wire fraud: these are still the payment methods most susceptible to payment fraud today. AFP research found that 66% and 39% of financial professionals reported fraud activity via these two payment types in 2020. However, check fraud has declined in recent years as fewer organizations are using checks for B2B payments.
- Deepfake: voice fraud is a relatively new method of attack but one that has proven highly effective. As the name suggests, a criminal fakes the voice of somebody else with software that can successfully copy his/her voice via a small audio sample.
- Ransomware attacks: in a ransomware attack, a company’s internal system is compromised (usually through email phishing). Users are instructed to either pay a ransom or permanently lose access to their systems.
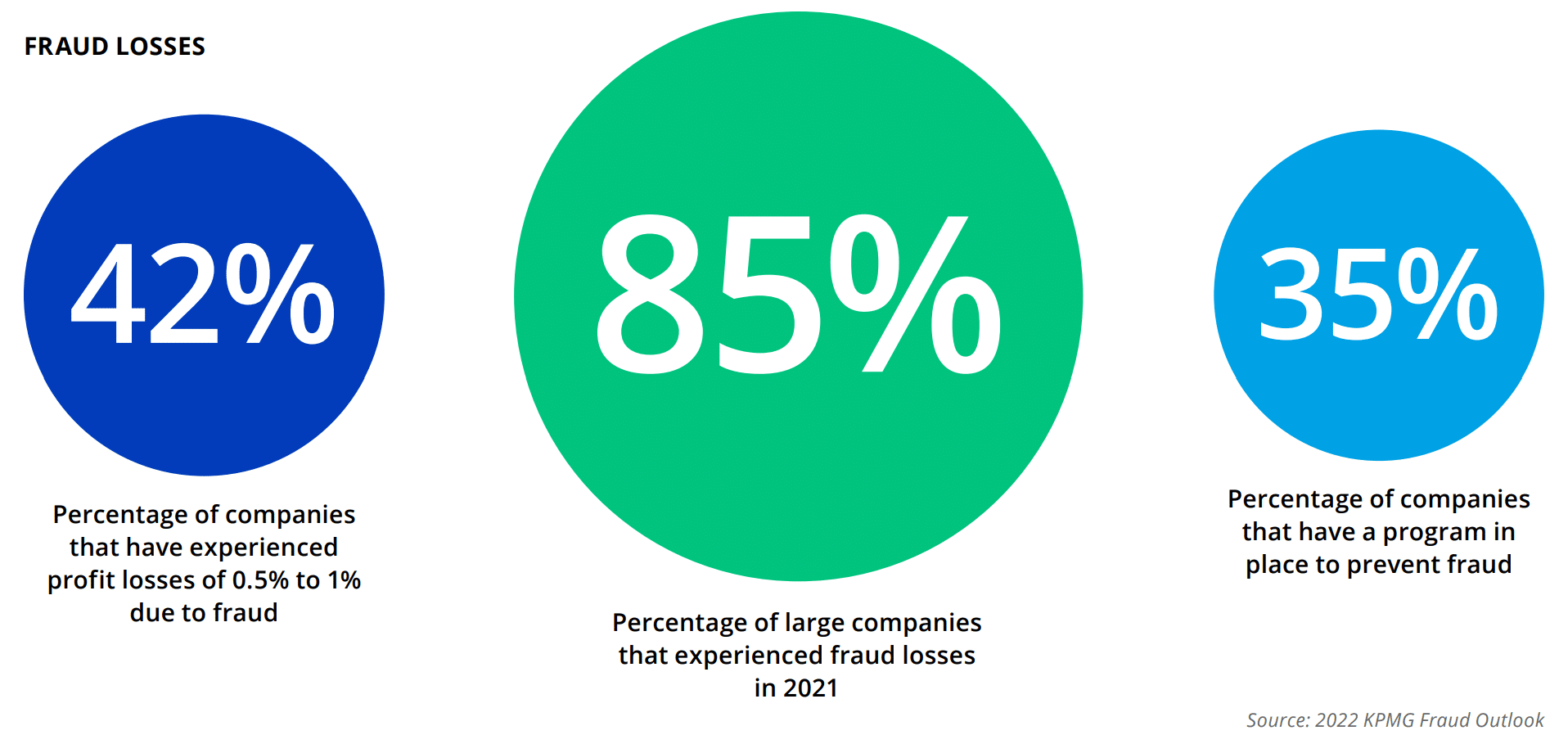
Who Is Responsible for Fraud Prevention in a Company?
In modern enterprises, payment fraud prevention is a shared responsibility. That is also one of the reasons why it is challenging to stop payment fraud from happening.
The typical payment process owner in a company lies within the office of the CFO, most often being the treasury team. There is also the Account Payable (AP) team who processes supplier payments and the Human Resources (HR) team who ensures salary payments are paid on time.
These teams usually use their own specialized systems to process these payments. For example, treasury usually uses Treasury Management Systems (TMS) or a banking portal offered by a bank, while the HR team uses a payroll system due to confidentiality and data protection requirements.
From an IT standpoint, the CISO office ensures that the payment systems in use fulfill the IT and cybersecurity requirements.
Main Challenges with Fraud Prevention
When it comes to corporate payments, there are three major areas of vulnerability in an organization that usually lead to payment fraud:
Technical Vulnerability
- Insufficient encryption
- Disparate ERP or siloed back-end systems
- Data unsynchronization
- Lack of end-to-end automation
Processes Vulnerability
- Lack of process standardization
- Lack of visibility
- Manual interventions throughout the payment process
Human Vulnerability
- Inadequate training and lack of awareness about payment fraud
- Errors or lack of experience in judgment
- Lack of communication especially among different teams
A simple rule of thumb is: The more decentralized a company is, the more manual steps are involved in the payment processes, the weaker the defense vector is, and the bigger the challenges are to prevent payment fraud.
What Are the Consequences of Payment Fraud?
Many high-profile fraud cases have captured media attention over the past years. They cost the victims both monetary and reputational losses.
One such case was with Google and Facebook. A Lithuanian man called Evaldas Rimasauskas pleaded guilty in 2019 for committing accounts payable fraud by sending phishing emails to Google and Facebook employees with fake invoices and luring them to wire millions of dollars to his own bank accounts. The two companies were reported to have lost more than $100 million in total.
Another famous fraud case that was highly visible in the media was with Nike. A former marketing manager of Nike scammed nearly $1.5 million in Nike proceeds for his own use by committing internal fraud. He was said to have forged his friend’s signature on checks and withdrew much of the money without his friend’s knowledge.
Insider fraud can be very hard to prevent or detect because the signals might only be captured long after the fraud has been committed, or never detected at all.
Use of Fraud Detection Solutions
Today, treasury and finance professionals have many fraud detection solutions at their disposal. It is important to have control and monitoring mechanisms in place on top of employee education.
The following best practices give a good start.
- Offer employee training programs with fraud simulation tools to increase awareness about payment fraud
- Design an end-to-end automated payment processes to standardize payment controls and audit to prevent fraud
- Standardize the workflows to lower the vulnerability coming from silos and lack of communication between the teams
- Adopt AI-powered real-time screening of all payments data to identify and block suspicious transactions for further validation
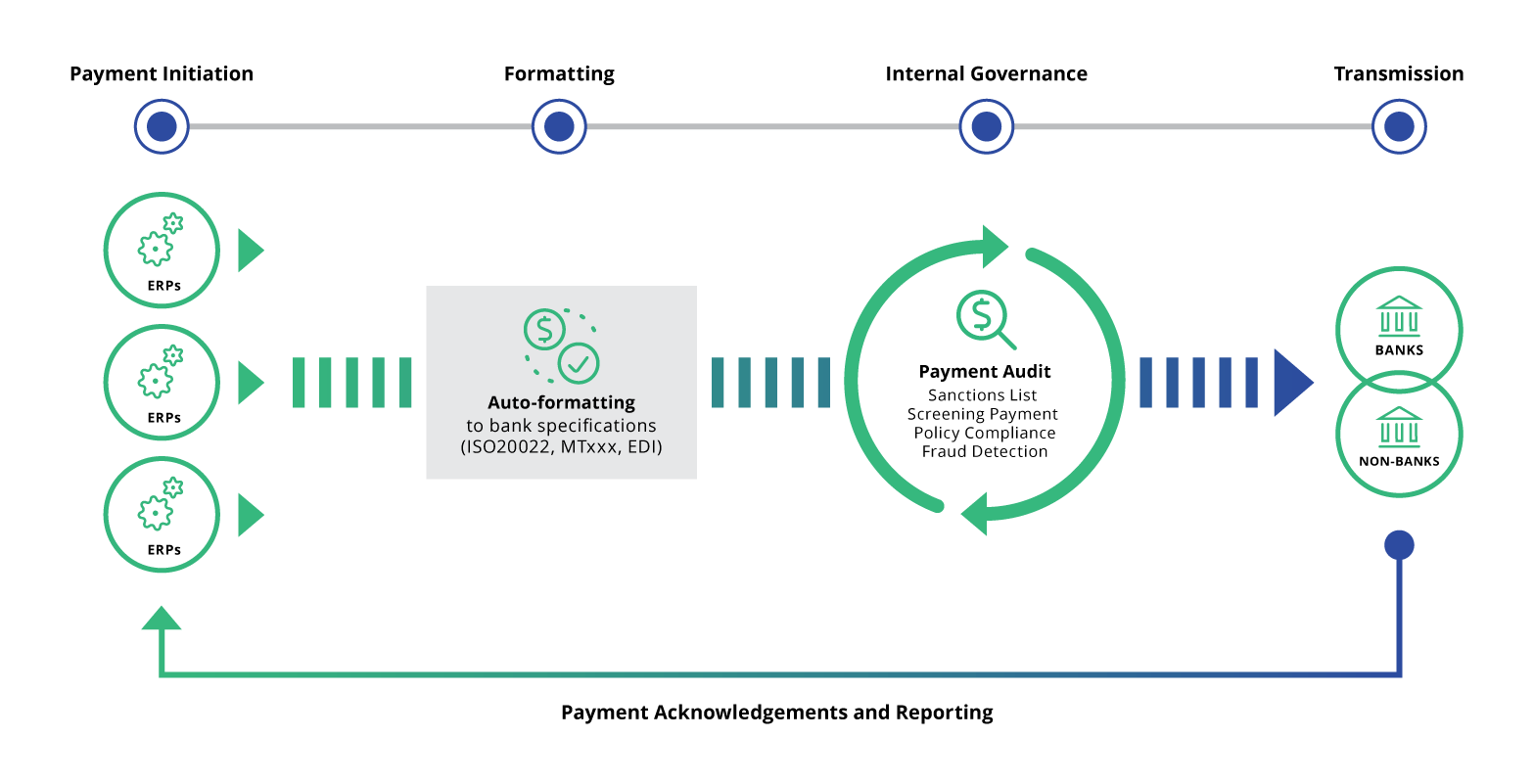
Use of a Payment Hub to Prevent Fraud
When you design workflows to prevent fraud, take the following checklist into consideration:
- Duplicate payment check
- BIC validation – including beneficiary country
- Bank account owner validation
- Sanctions list screening
- Payment policy compliance
- Payment pattern check with rules and AI
For an example of how using the above controls in conjunction with Kyriba’s treasury and finance software successfully stopped payment fraud in its tracks, see how Kyriba helped prevent a payment fraud case worth of $8m.









