eBook
The Perfect Storm of B2B Payment Fraud: How to Defend Your Treasury Before It’s Too Late

B2B payment fraud is one of the top concerns keeping CFOs and treasurers up at night, having increased in importance due to the proliferation of spear-phishing, data breaches and the resulting loss in company value. In addition to the direct financial losses, the indirect losses can be devastating. Falling stock market value, loss of confidence from investors, customers and partners, lawsuits and fines are all possible. The reputations and careers of you and your colleagues could also be in severe jeopardy.
You needn’t become the next victim. This eBook outlines how a more educated, better-trained treasury team, combined with the right process and technology solution in place, can effectively protect your organization from both internal and external payments fraud.
56% of US companies were affected by payment fraud in 2022
- 43% of organizations have been targeted more than once.
- 55% of successful fraud attempts are perpetrated through credential or information changes on legitimate payments.
- 33% of companies indicated that business email compromise (BEC) and phishing were the methods used to perpetrate the fraud attempts.
- 24% of companies that fell victim to fraud lost more than $100,000, and more than 5% lost more than $1 million.
- Companies still rely on manual and inefficient processes to prevent fraud.
- 82% of senior leaders consider fraud prevention to be a top priority for 2023.
Source: US Companies and B2B Payment Fraud Report by TrustPair and Giact, 2023
Table of Contents
A Multi-Layered Approach Necessary to Combat Fraud
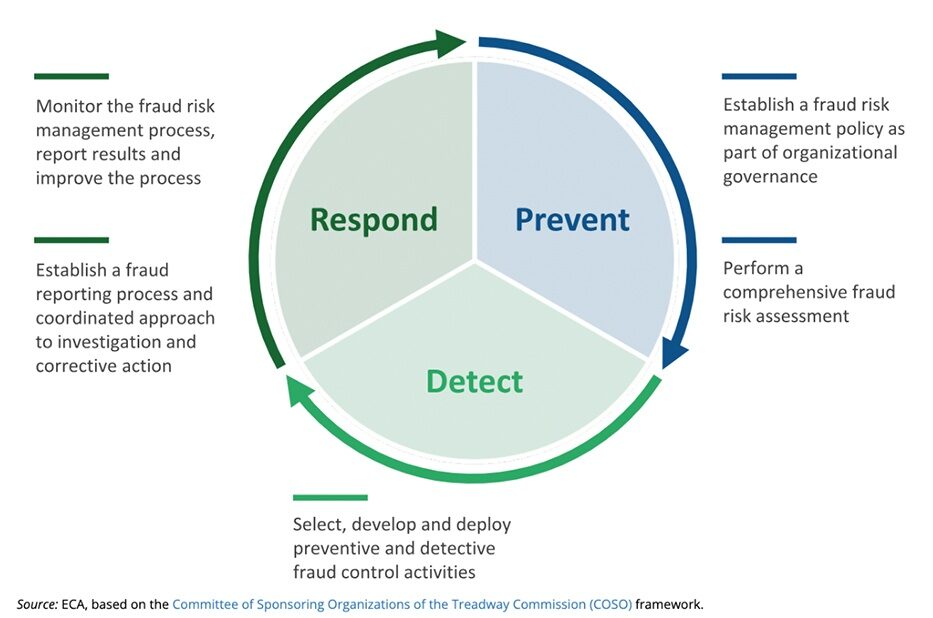
Threats are ever-evolving, so should be the measures being taken to tackle fraud. However, as the survey data above indicates, even in the year of 2023, many companies still rely on manual and inefficient processes to prevent fraud. Some may have a system in place, yet a system alone is not enough to holistically prevent fraud. We find the following Fraud Risk Management Process framework from the European Court of Auditors a great guiding principle for any global organizations who are in the process of bringing their fraud defense to the next level.
It is important to remember that encompassing prevention, detection and response is crucial for safeguarding an organization’s financial integrity. In this ebook we will also elaborate on some of the most important best practices in each area.
- Prevent: The first line of defense, prevention involves implementing robust internal controls, stringent policies and technology solutions. Education and training staff to recognize fraud risks, employing multi-factor authentication and setting up firewalls are part of this proactive approach. By creating a hostile environment for potential fraudsters, organizations can nip many threats in the bud before they materialize.
- Detect: Despite the best prevention efforts, some fraud attempts may penetrate the defenses. That’s where detection comes into play. Continuous monitoring of transactions, regular audits, employing artificial intelligence to recognize unusual patterns, and establishing whistleblowing mechanisms can help in early detection of fraudulent activities. The quicker a potential fraud is detected, the lesser the damage it is likely to cause.
- Respond: A well-orchestrated response strategy is crucial for minimizing the impact of a fraud incident. This includes having a clear plan in place, with designated responsibilities and protocols for escalation. Timely legal action, communicating with stakeholders, recovering lost assets, and taking corrective measures to prevent future incidents are part of this phase.
Together, these three pillars create a comprehensive, ongoing and dynamic process against B2B payments fraud. By combining vigilance with proactive measures, organizations can stay ahead of fraudsters, protecting both their assets and reputation in the increasingly doom and gloom scenario of corporate fraud.
Future 1: Fraud Risk Management Process framework from the European Court of Auditors
What are the Different Types of Payment Fraud?
There are a broad range of both internal and external threats that can breach the integrity of an organization’s corporate cash. In order to understand how your organization can become more secure, it’s critical to know what vulnerabilities you may be exposed to.
Examples of vulnerabilities:
- External hacking of treasury systems and files by third parties, exploiting data security flaws.
- Inappropriate employee access to server rooms / internal networks, resulting from weak physical and data security processes.
- Fraudulent payments sent by employees to banks, both willfully or based on bad judgment (often as a result of social engineering, “phishing” attacks).
- Fraudulent purchase orders and invoices created by internal employees to related third parties.
- Settlement instructions direct funds to unauthorized accounts.
- Suboptimal financial trades being made by employees in return for personal gain.
- Non-employees remaining signatories on current bank accounts after their departure / termination.
- Infrequent or inefficient reconciliation of accounts, leading to fraudulent transactions remaining unnoticed.
Protecting your organization’s financial integrity is of the utmost importance – especially in today’s digitally connected business and IT landscape, where fraudsters constantly seek vulnerabilities to exploit. Understanding the various types of fraud that can pose a threat to your organization is crucial for implementing effective preventive measures.
How to Build Application Security
Strong Password Controls
Weak login and user authentication procedures are among the most common vulnerabilities exploited by potential fraudsters. Attackers prey on weak passwords. The first priority for organizations should be to eliminate a single point of failure – e.g., one hacked password shouldn’t allow access to treasury and financial systems.
Industry practice is to – at a minimum – implement dual-factor authentication. Bank portals often use this technique, offering tokens (or key fobs) that randomly generate a second password when the original User ID and password are correctly entered.
Most software platforms support bring your own device (BYOD) so that your smartphone can be used to receive the one-time ‘second’ password. Other options include YubiKey, which is often used in EMEA.
However, dual-factor authentication alone is not considered best practice. Multi-factor authentication techniques combine different login and authentication strategies together to provide the best possible protection for corporate systems. Implementing multiple levels of user authentication simultaneously can significantly enhance the security of treasury data and systems, offering robust protection against unauthorized access.
It is recommended to combine two or more of the following to prevent unauthorized access:
- Dual-factor authentication – use an independently generated one-time password from your smartphone or independent token.
- Single Sign On (SSO) and LDAP authentication.
- Internet Protocol (IP) filtering – restricting login to predefined IP addresses.
- Numeric keypad, where numbers within a password must be selected by mouse instead of being typed.
- Dedicated Virtual Private Network (VPN) access.
Digital Signatures
Digital signatures are a critical tool to help banks authenticate transmitted payment files sent from third party systems, such as TMS or ERP. Digital signatures are personal digital identity solutions based upon a Public Key Infrastructure (PKI).
SWIFT’s 3SKey, considered the industry-leading digital signature solution, can be applied:
- Internally as part of a payment approval workflow, and
- Externally to authenticate the payment batch, confirming to the bank that all payments are accurate and valid. This not only helps validate the payment but also decreases propensity of repudiation by the bank.
- Externally as part of an eBAM workflow to authenticate bank account changes.
Use of digital signatures, combined with strong password controls and a centralized payment workflow, dramatically eliminate opportunities for payments fraud.
Improving Data Security In the Cloud
For cloud service providers, data security is top of mind, especially in mitigating internal fraud risk for financial teams. The right cloud service provider will have servers housed in fully redundant, secure global data centers, offering optimal physical and data security, as well as industry-leading uptime, backup and data recovery processes. In addition, treasury teams should invest in a provider that can fully support data encryption at rest.
It is also important to use a provider that works with respected data security technology providers. Regular SOC1 and SOC2 Type II reporting is also critical for data security and should come into play when looking for a cloud service provider.
CIOs and CTOs are the first to agree that cloud solutions can improve data security, presuming the right investments by a cloud solution provider are made to protect treasury data.
The following are some measures a cloud service provider can leverage to keep your data safe. Make sure you include those into your RFP when evaluating potential vendors.
- High performance disaster recovery
- Data encryption at rest
- SOC1 and SOC2 audit reporting
- Frequent penetration testing
The median duration of corporate fraud – the amount of time from when it commences until it is detected – is 12 months.
Source: Association of Certified Fraud Examiners bi-annual survey on corporate fraud, 2022
Visibility and Control Over Global Bank Accounts
Insufficient visibility into bank accounts and bank signatories are a recipe for disaster in treasury management. Too often, bank account approvers and signatories aren’t centrally known – or worse – may have left the organization years ago. Organizations are yet to recognize that ‘offboarding’ is as important as ‘onboarding’, especially when it comes to the staff members who have the payment approval rights. Maintaining visibility and control of bank accounts also becomes extremely difficult as organizations grow geographically or via acquisition.
Best practices can be used to reduce risks and increase controls:
- Centralizing visibility into accounts, authorized signers and all bank account documentation.
- Structuring workflows to require all bank account activity to be tracked and approved using predefined controls and limits.
- Setting up reconciliation procedures, both with your banking partners, and your corporate HR system, ensuring account signers are tied to employee lists.
Employing these processes not only reduces your organization’s potential exposure to both internal and external fraud, but also helps you comply with local and international regulations, such as FBAR reporting.
Further, visibility into bank accounts combined with effective bank fee analysis enables your organization to identify and close underused or dormant accounts, not only reducing your banking costs but also removing the risks of those less active accounts being exploited for fraudulent purposes.
Ensuring Standardized Payment Workflows
Spear-phishing in treasury is the most dangerous fraud attempt because cybercriminals are specifically targeting you. It focuses on payment workflows because success offers immediate payoff – a fraudulent transfer of funds to the wrong bank account.
While implementing strong password controls improves protection, standardizing payment workflows to ensure payment procedures are consistently followed is also critical. Targeted attempts prey on a single exception to policy; only one mistake is needed to create a fraud opportunity.
Standard practice is to implement multiple, standardized levels of approval and ensure approvals are electronic, tied to the separation of duties within the treasury system, and aligned to dollar limits. Many treasury teams will use digital signatures for internal payment approvals (as well as for external authentication of payments).
Organizations that separate the payment workflow – e.g,. use internal systems and bank portals separately for initiation and approval – increase the risk of exploitation.
It was simply unsustainable to continue logging in to each individual e-banking platform in order to approve payments.”
—Andrew Nicholson, Graff Diamonds CFO
Best practice is to manage the complete workflow for all payments in one system which offers a complete electronic ‘paper trail’ for that payment, from initial request through to transmission. This also allows the payment acknowledgements (up to four levels) to be integrated with the payment workflow.
Many organizations also centralize treasury and supplier payment transmission via a central payment hub to ensure treasury has complete transparency of every outgoing payment, globally. This allows complete oversight over all outgoing cash flows, in addition to saving costs.
Standard Settlement Instructions (SSI)
Settling financial trades is an increasingly exploited opportunity for internal financial fraud. Entering into financial trades – investments, foreign exchange, derivatives – is a daily activity for treasury teams.
For typical trades with your bank, it is common for standard settlement instructions (SSI) to be implemented in advance at the bank. However, for non-typical trades or for transactions with non-bank counterparties, SSI may not be in place. This creates an opportunity for fraud where wire transfers to settle trades can be fully or partially redirected to unauthorized bank accounts.
Standard settlement instructions (SSI) within your financial systems improve efficiency as well as avoiding redirection of funds to unauthorized accounts. It is best to find a solution that supports electronic workflows and integration of trading and payments activities to help minimize the potential for internal fraud.
Key steps to implement include:
- Electronic recording of financial transactions in your treasury system, with approvals and limits applied so a full audit trail is available for review.
- Payment templates should be automatically attached to each trade. Additional approval should be required to edit/remove the payment template, with all activity tracked in the audit trail.
- Reconciliation of the trade tickets between the counterparties and the treasury system should be performed on a standard frequency – with oversight of the process to ensure no exceptions slip through.
Never Lose a Battle, and Win the War
A robust technology solution is a critical element of the security equation. However, even with a sophisticated payment fraud prevention solution in place, treasury teams need to ensure they are not the weak link, inadvertently exposing the organization to fraud.
Therefore, it’s essential that companies educate their staff about the ways that fraudsters can dupe employees via social engineering, either into revealing sensitive banking data, or even into sending cash and payments themselves. Employees must be aware of internal processes for creating and sending payments, how to spot a potentially fraudulent request, and even more importantly, where and how to report any suspicious activities.
To reduce internal fraud, leveraging AI technology that monitors and singles out potentially fraudulent transactions is no longer an IT heavy duty, as there are many turn-key solutions that can be readily deployed. It is also critical to maintain thorough audit trails to ensure that any investigation can run as swiftly as possible in case of a fraud incidence.
You can also work with your organization’s Chief Information Security Officer (CISO) – or, even better, a third-party security organization – to try and exploit flaws in your system. These results can then be fed back into the organization to improve your processes.
In the face of increasing fraud risks, having the right processes, technology and staff awareness in place, all under a well-defined framework to prevent, detect and respond, your organization is ready to orchestrate a battle-ready defense against fraud.









